

Know who and what is connected to your network at all times.
Identify vulnerabilities on your network to avoid exploitation and compromise.
Find insecure settings in Office 365 & G Suite to enhance your security posture.
Identify malicious behavior and potentially compromised systems.
Know when suspicious activities happen in your environment.
Detect threats against your critical infrastructure, both on-premise and in the cloud.
Correlate and analyze security event data from across your network.
Isolate infected endpoints to prevent malware from spreading.
Respond to threats quickly to minimize damage and prevent further escalation.
A modern cybersecurity solution built for modern infrastructures. Our platform collects and normalizes events from disparate sources across your network so they can be analyzed and correlated using the latest threat intelligence.
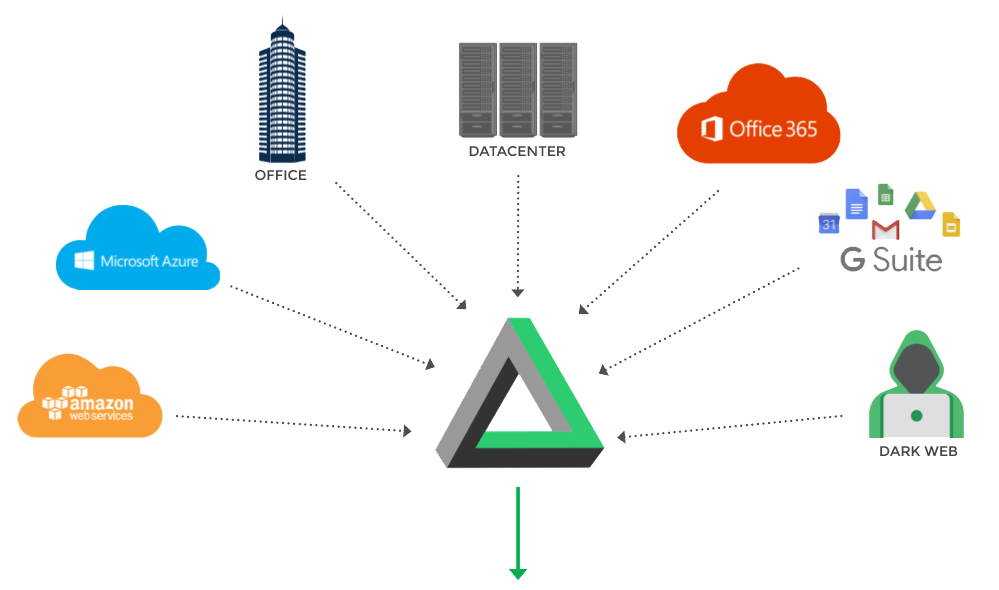
We monitor your network, discovering vulnerabilities, investigating attacks, and alerting you to real threats.
The technology platform is monitored by expert security professionals who review and investigate all potential threats, weeding out the false-positives and identifying real threats. Our team then alerts you to the issue, with easy to understand insights and actionable remediation steps, enabling you to respond quickly to isolate and remediate the threat.

We utilize state of the art technology, deployed on your premise or in your cloud environments. Our platform monitors your environment, collecting and correlating data from sources across your network, and alerts us to any potential cyber threats. Backed by the Open Threat Exchange, our platform is constantly updated with over 14 million threat indicators every day, contributed by a global community of threat researchers that spans 140 countries and over 65,000 participants.

The technology platform is monitored by expert security professionals who review and investigate all potential threats, weeding out the false-positives and identifying real threats. You only hear from us when the threat is real and verified, so you avoid alert fatigue.
When a real threat is identified, our team alerts you to the issue with easy to understand insights and actionable remediation steps. We work with your existing IT department, enabling them to respond quickly to isolate and remediate the threat.
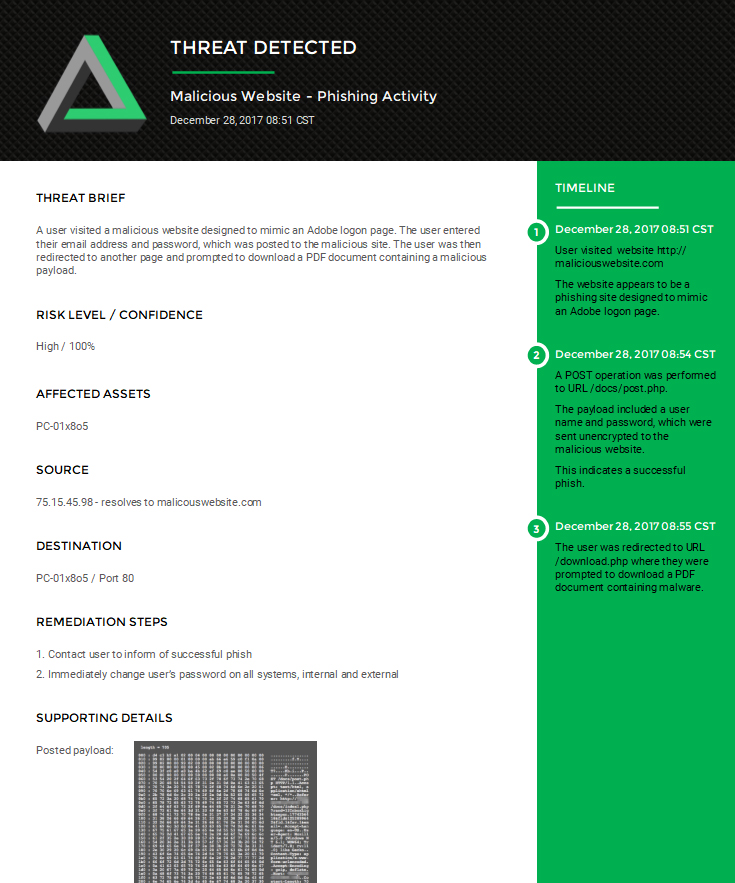

We scan your network weekly for vulnerabilities, identifying weak spots in your network, and allowing you to take proactive action before attackers are able to exploit them. Plus, we monitor the dark web for stolen company credentials.